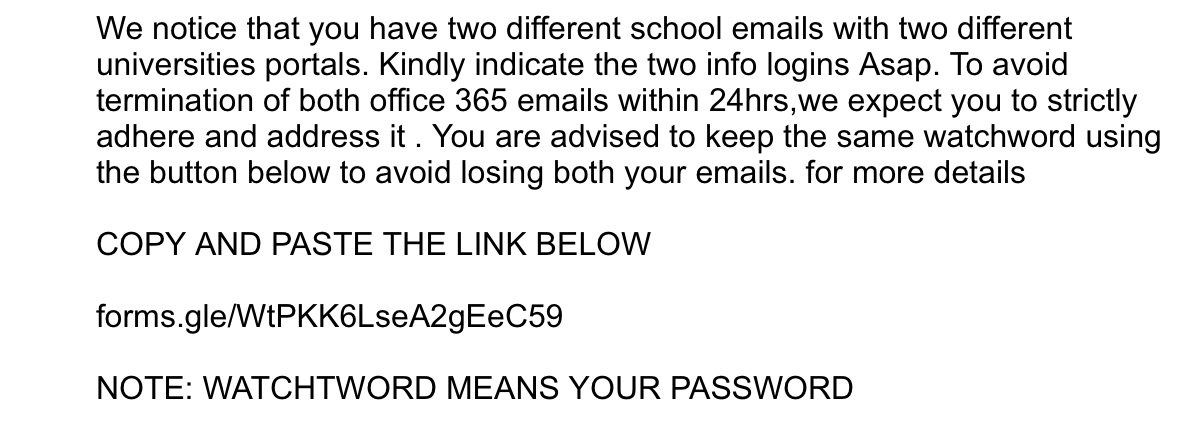
Several students received phishing emails in July and August about changing their university-affiliated email passwords.
Now, the university’s Information Technology department is working on educating the campus community about phishing emails.
James Raber, associate chief information officer, compared the concept of phishing to a bad performance from actors.
“Phishing is a behavior,” Raber said. “You know, we have bad actors that try to trick people into providing information they would not normally give up.”
Raber said that phishing can occur over multiple mediums, such as email, phone or social media, with one objective in mind.
“Oftentimes the goal is to get somebody to give up either personal information or login credentials,” he said.
Tom Schindler, associate director of Information Technology and a member of the Information Security team, said that he thinks the cause of the phishing email incident from August was a result of reused passwords.
“More than likely it’s students that had reused passwords or infected machines that captured their password,” Schindler said. “The attacker was able to get into their account and then send these emails out.”
Raber said the IT department’s monitor system allowed for a quick response to those affected by the phishing emails.
“The first time that we got a notification, the email engineers . . . hopped on, took inventory of the situation trying to figure out what happened, who received it,” Raber said.
Since the phishing emails were sent out during the summer, there have been two stages of remedying the situation, Raber said.
“One is we want to clean up the environment,” he said. “Make sure that those emails sitting in people’s inboxes are eliminated as quickly as possible.”
The following step focuses on the email that has been compromised and how to protect it.
“The other aspect of that though is the account that was compromised, trying to make sure that account is put into a better spot where the bad actor can no longer do any more damage,” Raber said.
To protect the compromised account from further attacks, the IT department will change their email passwords and enact other security measures.
“Once we get alerted, we’ll secure the account by changing the password, revoking all the sessions,” Schindler said. “Then what our email team does is actually goes and searches for all those messages that were sent out, destroys them, deletes them.”
Phishing emails have occurred in entities outside of the university, like other higher educational institutions and businesses featuring similar messages, Schindler said.
Schindler said the links attackers send may take the user to websites that may appear to be Microsoft when they are not.
“It brings up a log-in page that looks like a Microsoft page and then they type in their credentials and that’s how they end up getting their account compromised,” he said.
Since email accounts of alumni are still active, they can also be vulnerable to phishing attacks.
“Once someone graduates, sometimes that account becomes somewhat dormant,” Schindler said. “Maybe people aren’t paying attention to what’s happening with that account because they don’t use it anymore. Then their password ends up being breached.”
To avoid those vulnerabilities, Schindler said to not use the same email account multiple times.
“I listen to a privacy person and he’s always like, ‘You want to make sure you don’t have all of your eggs in one basket,’” Schindler said. “I was listening to something he was talking about some guy who lost his Google account because of the situation he was in and that meant he lost his phone.”
Raber said there are ways that students and faculty can protect their accounts from phishing incidents.
“The thing I would recommend to anyone is use something like a password manager like LastPass,” Raber said. “The platform creates a highly complex [password] for me and it works seamlessly across all of my devices.”
Another way to avoid a phishing attack is by installing Multi-Factor Authentication, which involves entering another factor like a six-digit code after entering a username and password.
“Set Multi-Factor Authentication on all your accounts,” Raber said. “A lot of time it’s an optional thing to turn [on], just turn it on, you should do that for everything.”
Raber also recommends only using certain types of Multi-Factor Authentication.
“If you have an option to use an app-based Multi-Factor, you absolutely should, things like Microsoft authenticator for LastPass authenticator,” Raber said.
For phishing emails, there are a few signs to be aware of to determine the validity.
“Oftentimes, [the emails are] hastily written and have misspellings or poor grammar,” Raber said.
Since the university switched a majority of students’ emails to Microsoft last semester, students can receive notifications that inform them that these emails are not coming from Kent State, Raber said.
“When you get an external email, it has a label on it declaring that it is an external message,” Raber said. “If you have something that looks like it’s from Kent State but it has that label on it, be suspicious.”
Raber said students and faculty can stay alert by visiting the SecureIT website where they curate news and information to help people keep their accounts protected.
“Pay attention to stuff, like just because we’re dealing with [Multi-Factor Authentication] bombing right now that doesn’t mean that’s going to be the risk that we’re going to see six months or a year from now,” Raber said.
Adriana Gasiewski is a staff reporter. Contact her at [email protected].